IMSI-catchers are significant to both security forces and the general public. While law enforcement agencies consider them as crucial tools for crime prevention, they pose a potential threat to privacy for the wider population. Knowledge about IMSI-catchers empowers individuals to adapt their communication and security measures accordingly. Striking a balance between security interests and safeguarding individual rights necessitates transparent discussions and clear legal frameworks to ensure adequate protection for all.
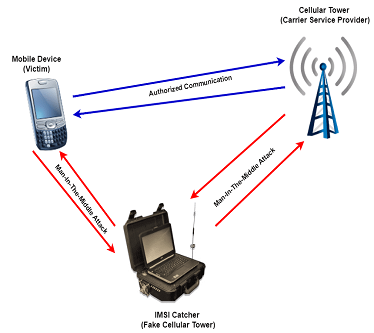
An IMSI catcher, also known as a Stingray or Stingray device, is a tool used to intercept conversations, read SMS messages, and gather other mobile phone data such as IMSI (International Mobile Subscriber Identity) and IMEI (International Mobile Equipment Identity). The IMSI catcher simulates a mobile network cell of a service provider, enabling it to attract nearby mobile phones and extract their data. These devices have a range of approximately two kilometers, meaning they can potentially be deployed over a significant radius. The use of an IMSI catcher poses a serious threat to the privacy and security of mobile phone users and requires appropriate measures to defend against it. (Image sources: SECINTEL-Security & Defense Technologies, FirstPoint-mg.com)
Functioning of an IMSI Catcher
The IMSI catcher functions by simulating a mobile network base station of a service provider. When a mobile phone comes within range of the IMSI catcher, it automatically connects to the device. During this connection, the IMSI number, which is stored on the SIM card and used to identify the user with the mobile network provider, is queried.
Through this connection, the IMSI catcher can monitor all communication traffic, including phone calls and SMS messages. Not only is the exact content of the communication interceptable, but also metadata such as the timing, location, and duration of the communication.
It is important to note that the use of an IMSI catcher is illegal. However, it is technically possible to build an IMSI catcher oneself starting at a price of approximately 300 pounds or to purchase ready-made devices starting at around 1,500 pounds.
There are reports that illegal IMSI catchers are frequently deployed in crowded locations such as train stations, airports, or other highly frequented areas. This allows criminals to intercept large amounts of mobile network data. Therefore, it is of great importance to take appropriate security measures to protect oneself against potential IMSI catcher attacks.
Utilization of an IMSI Catcher
IMSI catchers are used by the government in Austria for surveillance purposes. While there were approximately 32 deployments of IMSI catchers per day in 2008, the number dropped to 122 per year in 2018. According to the Ministry of the Interior, these devices are only utilized to gather information and locate mobile phones.
However, in general, an IMSI catcher can be employed not only for directly eavesdropping on conversations and SMS messages but also for extracting call metadata and identification data such as IMEI and IMSI.
In many countries, IMSI catchers are commonly deployed during demonstrations to identify participants.
IMSI-Catchers: Risks, Defense, and Responsibility
Unfortunately, actively defending against an IMSI catcher is challenging as most individuals do not realize when they are being intercepted. This is partly due to the inability to securely verify the authenticity of a connection with a mobile network station.
In some countries, such as Austria, the use of IMSI catchers is even permitted without judicial permission, thanks to an amendment to the Security Police Act since January 1, 2008. This provision has faced strong criticism from privacy advocates, raising concerns about abuse and privacy violations.
Despite limited options for direct defense against IMSI catchers, there are measures that can be taken to minimize the risk. One approach is to use encrypted communication channels, such as encrypted messaging apps or voice-over-IP services. Employing Virtual Private Networks (VPNs) can also help enhance communication security.
It is also advisable to exercise caution in where and how one uses their mobile phone. Avoid using unsecured public Wi-Fi networks and be mindful of suspicious or unusual network activities on your device.
However, it is important to note that protection against IMSI catchers ultimately relies on the actions taken by law enforcement agencies, legislators, and network operators, who must undertake appropriate steps to ensure the privacy and security of mobile phone users.
5G: Enhanced Protection against IMSI-Catchers?
The advent of 5G technology brings the potential for improved protection against IMSI-catchers. With its advanced encryption algorithms and enhanced security features, 5G networks aim to provide a higher level of privacy and integrity for mobile communications.
One of the key security enhancements in 5G is the implementation of stronger encryption algorithms, making it more challenging for IMSI-catchers to intercept and decipher sensitive information. Additionally, 5G networks incorporate improved authentication protocols, reducing the risk of unauthorized access and mitigating the effectiveness of IMSI-catcher attacks.
Furthermore, 5G networks employ enhanced security mechanisms, such as secure network slicing and network function virtualization, which help isolate and protect user data from potential interception. These features contribute to creating a more secure communication environment, reducing the vulnerability to IMSI-catcher threats.
However, it is crucial to acknowledge that while 5G technology offers advancements in security, it is not entirely immune to potential vulnerabilities. Ongoing vigilance, regular security updates, and collaboration among stakeholders, including network operators, device manufacturers, and security experts, are vital to ensure the ongoing protection of mobile communications against IMSI-catchers and other security risks.
Together we can make a difference!
Become a part of the MOORE PROTECTION COMMUNITY and subscribe to our newsletter and find out about many interesting topics through our blogposts.
Risk posed by IMSI-Catchers in Personal Protection
IMSI-catchers pose a potential risk in personal protection. As they can intercept communication and gather personal data, they become a tool for potential attackers or stalkers. Individuals with heightened security needs should be aware that IMSI-catchers could be employed and take appropriate security measures, such as using encrypted communication channels and regularly checking devices for suspicious activities. Engaging in dedicated security consultation can also be helpful in minimizing the risk.